3 TOP CYBER SECURITY THREATS OF 2016, AND HOW TO COUNTER THEM!
WEDNESDAY’S COFFEE BREAK WITH <PETER ZINN>
As everyone and everything is going online, the flipside of digitalization becomes bigger and more visible.
Cyber security is important, but it still does not get the attention it deserves.
Why? Too difficult, too expensive, too vague?
Our cyber security expert, Peter Zinn – sheds the light behind the scenes of cyber security, giving you a well informed insight on the top 3 cyber security threats in 2016 – and how to counter them!
D
3 TOP CYBER SECURITY THREATS OF 2016, AND HOW TO COUNTER THEM !
Quick question:
Do you know how many companies from the Fortune 500 list have been hacked?
Cybercrime is a very real topic, not only for the biggest companies, but for all of us. This very moment hackers may be out there busy trying to infect your systems in various ways. How can you secure yourself from an intangible and invisible threat? And is it even necessary?
You will find all the answers in this article!
Let’s have a look at three current threats amongst the many to give you a quick glimpse into the the world of rogue zeros and ones.
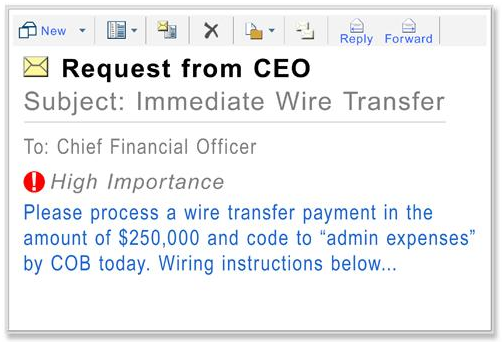
Threat 1: “CEO fraud”.
What it is
Technically CEO fraud is not even cyber crime, but since the attackers use emails, and since it causes substantial losses, let’s give it some attention. Here is how it works:
The CFO [Chief Financial Officer] gets an email from the CEO with the request to quickly transfer a large amount to some account. The email of course is fake, but it looks legitimate. There may be a reason in the email, but just as often there is not. There is a need for speed though. Sometimes there are extra instructions: “my business partner will call you and guide you through the process.”: Sometimes the email is all that is needed. The CFO transfers the amount, the CEO comes back from holiday or steps out of the meeting and finds out the company just lost a considerable amount of money. Ouch.
In case you think this would never happen in your company: According to the FBI, 2.3 Billion dollars have been lost to this scheme over the past 3 years worldwide. 11% of all US companies are attacked by this type of fraud. The winner, or rather loser, in this category to date is Crelan Bank in Belgium, who reported to have lost €70 million last January. So you better make sure that this would never happen in your company…
What you can do about it
There will always be people trying to impersonate the CEO, and with the wealth of information they have available on the internet they can be pretty persuasive. So a technical solution is out of the question. What we’re searching for is a procedural change. How about a simple rule:
The CEO will never give wire transfer instructions by email without a confirming personal phone call.
Problem solved. Yes, it is still possible for a good trickster to impersonate the CEO, but the threshold has been raised considerably.
Added bonus :
Companies who have implemented the above rule on average have better financial procedures and controls. They keep better track of their finances and hence have a lower financial risk profile. Not only are you less susceptible to financial attacks from outside the company, you’re also less susceptible to financial surprises.
Threat 2: Cryptoware
What it is
Imagine you’re working on your computer when suddenly a screen pops up. It tells you that your computer is locked and your files have been encrypted. And, unfortunately, it is right. It also tells you that if you pay a certain amount of ransom you will get the key to unlock your computer.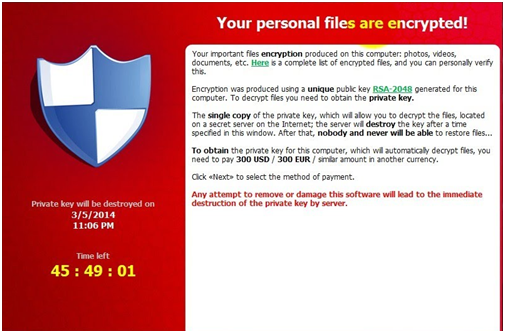
Millions of people have fallen victim to this attack. Sometimes, especially in the beginning, it was pretty simple to escape the clutches of the ransomware. Just as well, because paying wasn’t going to get you anything. But things have changed. Nowadays, when your computer is locked, it is really locked. And the malware is already evolving to automatically penetrate your network, jumping from computer to computer, looking for your shared data drive. Increasingly professional, cryptoware starts diversifying its market, with different amounts of ransom for private users and companies. And paying will get you cleared, but not disinfected….
For the various criminal groups behind cryptoware attacks this is a very lucrative business model. The percentage of paying customers is relatively high.
What you can do about it
Backup!
Make sure you have a copy of your important data at all times, and make sure it is offline. Many backups are connected to the network, allowing the cryptoware to encrypt the backup as well.Backing up is a simple time honored process that can easily be automated. With a backup system in place you no longer have to worry about your prime assets being taken hostage. You’re safe. If you regularly check whether your backup can be restored when needed…
Added bonus
Your hardware is not invulnerable. At some point one of your hard drives will crash and it’s content will be unrecoverable. A fire might destroy your high end RAID 6 NAS storage. Can you afford to lose all your data? Offline, off-site backup is the answer.
Threat 3: Persistence
What it is
Give it enough time and resources, anything can be broken. You may have heard of Advanced Persistent Threats before – APT was the security buzzword of 2015. But APTs are anything but new. It’s just another word for espionage, but now using technology. The most famous example is Stuxnet. In 2010, the Siemens Centrifuges in the supposedly secret Iranian nuclear facility in Natanz started malfunctioning and had to be replaced in large quantities. Only later a Belarusian security company found the culprit. Stuxnet had been able to infect the facility – that wasn’t even connected to the internet. Analysis showed that the malware took years and millions to make. Given enough time and resources anything can be broken.
APTs are no longer only the realm of nation states. The Carbanak group showed in 2015 that criminals are in the game too. They’re in it for the money. Lots of money. Carbanak would infect banks, take the time to learn everything about their systems, and then syphon off 10 million dollars. And as always in the world of cybercrime, what is successful gets copied. And spreads to other target groups. So don’t think you’re not interesting enough to be at the receiving end of an APT. You might be targeted by a RAT.
RATs – remote access trojans – allow hackers with little programming knowledge to take over your computer. With plug and play programs that they have bought for 20 euros they can do the same as the Carbanak gang, but at a smaller scale. They look around in your network and maybe add a line or two to the Excel sheet you use for your payroll.
What you can do about it
This is where we get to the answer of the question that opened this newsletter. And of course, the answer is: all of them. Now that doesn’t mean that they’ve all been hacked to the core, as in the Carbanak example. But someone broke in somewhere. The point: perimeter defense is not enough. A moat and a wall does not keep everyone out.
You have to assume that they (whoever these delusive “they” are) are already in.
How do you find an intruder? The answer is (life) network analysis. Check what’s going on in your network and analyse the behavior of it in order to recognize deviant behavior. First step: turn on logging, and analyse these logs. This analysis, which can be highly automated, will tell you what is normal in your network and what is not. Investigate the deviations: they could be a sign of an network intrusion.
Added bonus
What gets measured gets managed. By knowing your data streams you may get creative. In my time as a programmer I would sometimes grab a cup of coffee and just follow the data around as the program ran. Not seldom would I stumble upon inefficiencies, costing way too many resources. Or I would find out that some resources we paid for were actually not used at all. The same happens over and over for companies that analyse their network data. It wouldn’t be the first time if you found out that it was actually just one bottleneck that slowed down the system and that the planned investment in new workstations is no longer necessary.
Your crown jewels
In this article we glanced at only three cyber security risks. In real life, there are way more! Passwords, social engineering, DDoS attacks, SCADA attacks and much much more. It can be quite overwhelming. I’d be happy to give you a full overview of the battleground, but not here, not now. In this article I’d like to conclude with a good practice that practically all Fortune 500 companies have: they have identified their crown jewels.
What are your crown jewels? Which data on your computers or network is of vital importance for the survival of your company? Whether it’s the blueprint for a revolutionary computer chip or your client database – you should be able to identify what really matters to your company.
Focus your security on your crown jewels. Procedures, technical solutions, awareness training, they should all first and foremost be centered at protecting what really matters to you. The world of cyber security may look daunting and overwhelming, but if you keep that clear focus, you’ll find it’s not that much of a deal at all.
D
a little more about OUR INSPIRING SPEAKER:
 Peter Zinn is a speaker and trainer in two different fields of expertise! His skills revolve around the art of speaking and… the world of cyber security. As everyone and everything is going online the flip side of digitalization becomes bigger and more visible. Cyber security is getting more important, but it still doesn’t get the attention it deserves. Peter Zinn is the speaker for the job: he is able to talk about cybersecurity to both technical and general audiences. On the other hand, he is an accomplished speaking skills trainer, and speech coach for beginners. His clients include Nyenrode Business University, Kaspersky, Roche, Dutch Police, Toastmasters and other more. Peter speaks Dutch as well as English. Feel free to contact us to get additional information about our speaker and trainer.
Peter Zinn is a speaker and trainer in two different fields of expertise! His skills revolve around the art of speaking and… the world of cyber security. As everyone and everything is going online the flip side of digitalization becomes bigger and more visible. Cyber security is getting more important, but it still doesn’t get the attention it deserves. Peter Zinn is the speaker for the job: he is able to talk about cybersecurity to both technical and general audiences. On the other hand, he is an accomplished speaking skills trainer, and speech coach for beginners. His clients include Nyenrode Business University, Kaspersky, Roche, Dutch Police, Toastmasters and other more. Peter speaks Dutch as well as English. Feel free to contact us to get additional information about our speaker and trainer.
To discover more about Peter Zinn, click on this link to view his PROFILE.
See more of Peter Zinn’s INTERVIEW.